|
spankmeister posted:So the French network TV5Monde got hacked by IS, 11 channels down. They're actually fairly sophisticated from what I understand, and when they're not genocidin' people they're actively trying to keep the infrastructure of the lands they claimed up and running because their entire persona revolves around them being the one true "legitimate" state where all the Muslims have to go by law and life will be fun and happy and great (if you're not one of the people they kill). The reason why we haven't really seen them attacking the west much at all is more to do with their goals - they're not Al Qaeda, they're not trying to attack the "far" enemies. Their main goal right now is to claim land to make themselves more legitimate, and wait for America to come try to kick their asses, at which point they believe it's prophesied that they will win and that particular battle will start down the countdown clock to the apocalypse. The Atlantic did a pretty great write-up on the whole thing here.
|
|
|
|

|
| # ¿ Apr 29, 2024 09:32 |
|
Munkeymon posted:hahahaha he has a .computer domain hmmm... is funy.computer worth $40...
|
|
|
|
Nintendo Kid posted:
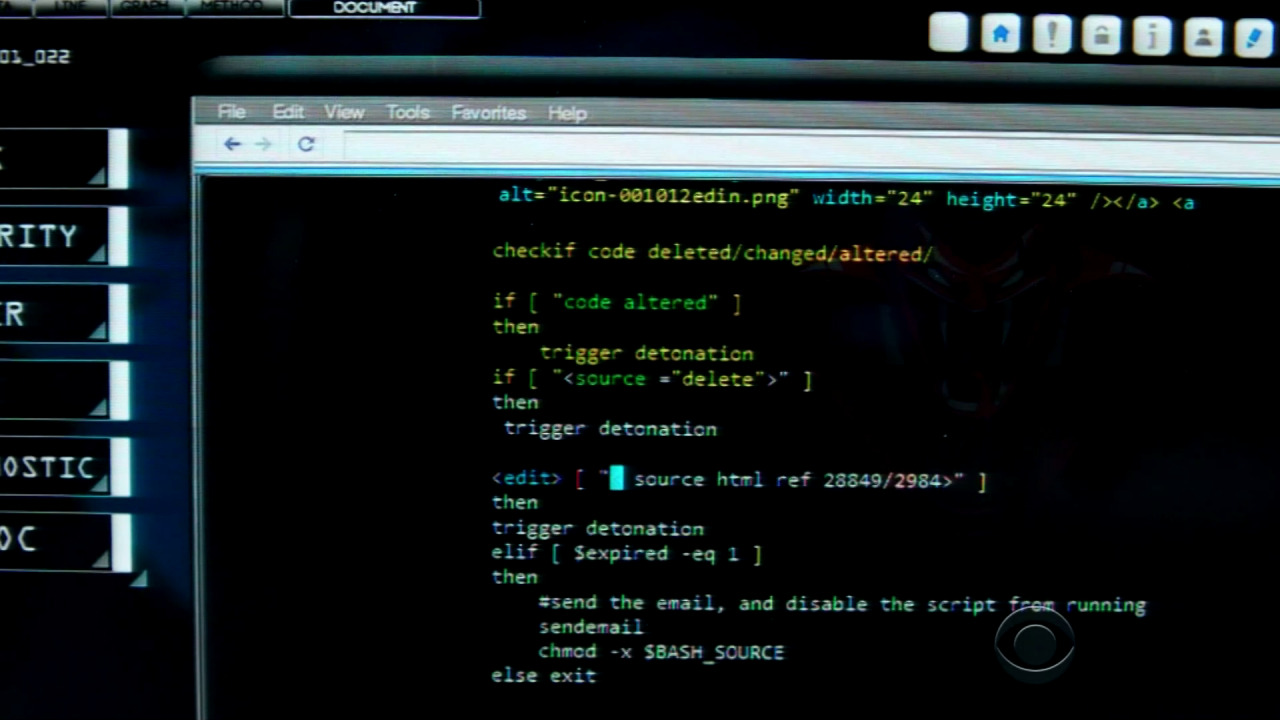
i'm the "checkif" operator
|
|
|
|
also i'm the random syntax highlighting that makes no goddamn sense
|
|
|
|
Carbon dioxide posted:So, Facebook felt it was necessary to "correct" some Belgian security report which showed that Facebook sucks. if you define "tracking" to be "following an animal through the woods using instinct and careful observation of the environment around you" then no Facebook doesn't do any tracking
|
|
|
|
Wheany posted:it's probably a screenshot of an editor with syntax highlighting for .sh files, but since the syntax makes no sense, neither does the highlighting idk half of it seems like it's trying to syntax highlight sh/bash but a bunch of it seems like they added it after the fact to emphasize the "bomb" parts, and other parts just make no sense at all.
|
|
|
|
FCKGW posted:http://www.fbi.gov/birmingham/press-releases/2015/ua-student-charged-with-unauthorized-access-to-university-computer tbf it sounds like a well-tailored phishing email rather than the sent-to-millions "hi i am from facebawk ur account has been hacked!!!! plz click here and answer some questions!" ones
|
|
|
|
Carbon dioxide posted:Back in my high school, it was fine to play browser games or do whatever on the library computers, as long as there weren't any kids waiting to use the computers for actual school work. They usually didn't even mind if you hacked it somewhat, because that allowed the IT guy to see where he could improve the system security. my school had a bizarre rule that chatting was banned but remote desktop / vnc was grey area don't ask don't tell sorta stuff so they'd kick you off if you tried to go to like, meebo, but if you remoted into your home computer and chatted that way it was fine.
|
|
|
|
quote:You know what? They were right - the company’s email system did NOT deal with this gracefully. nah "it's exchange" is pretty much enough of an answer.
|
|
|
|
~Coxy posted:"compose a new email" is only naughty when you do it in palemoon  at my company we had a barracuda content filter on everything which was mandated by one of our clients, not our choice. i say "had" because the CEO got annoyed with it blocking his "sites" and had IT completely bypass it so now it's just sitting there powered on to keep up appearances but it literally has no ethernet cables goin' to it at all.
|
|
|
|
Let's say that, hypothetically, my work network has been running an open, unrestricted SOCKS4 proxy exposed to the greater internet (and also our private network, so theoretically you could proxy into the private network if you knew the IP you were going to) for like a year now that we just noticed and fixed. Approximately how hosed do you think we should consider everything? Is this one of those "set fire to the office and start again down the street"-level things?
|
|
|
|
Truga posted:If someone abused it, you'd probably know after a year. Chances are people found it, laughed at it and posted about it on an internet forum, then went on with their lives. I can't set fire to him, he's been here way longer than I have and is best buds with the CEO. This is the same company that was running Tomcat 5 with the default password on ALL of the production servers for eight loving years before someone (me!) found it and freaked out. There were like 20+ servlets on each server that had been installed by bots and basically functioned as "allow executing whatever as root" services. Yes I'm looking for a new job.
|
|
|
|
Shaggar posted:tomcat doesn't have a default password for specifically that reason so they must have set up a password probably using the default example pw from apache.org which is probably like tomcat/tomcat. well it was "admin/admin" so if it wasn't the default it certainly wasn't set up right in any case. ultramiraculous posted:cheese-cube, the prod servers running unknown code were nuked and replaced with entirely new poo poo without transferring a single thing between the old and new stuff just to be sure. the proxy into our network is fun and new though.
|
|
|
|
herp derp can't edit
|
|
|
|
computer toucher posted:Does this actually work? i just tried it and it didn't work, and we're poo poo about updating our servers. Microsoft might have force-updated it though. EDIT: I got this: code:Shame Boy fucked around with this message at 14:43 on Apr 15, 2015 |
|
|
|
anthonypants posted:why does it have to be telnet and not like, netcat or wget or something because they're a windows user and they don't have any actually useful programs on windows
|
|
|
|
anthonypants posted:according to this tweet if you do this does a.png actually have to exist? because I'm getting 404. EDIT: tried it with a file I knew to exist and it returned 416 woo
|
|
|
|
anthonypants posted:it looks like you got a 416 on the telnet one too yeah but that was before i realized 416 was what we were looking for. security guy is patching it right now anyway, but it's the same security guy that allowed graph posted:r o f l so we'll see...
|
|
|
|
Mido posted:my car has the option of being 100% keyless my car just has a START button rather than a hole for keys, the only way to start it if the fob battery dies is to rub the fob against the START button for a few seconds while it does some powerless RFID poo poo.
|
|
|
|
Mido posted:i don't live in the future until I have to say the product of the day out loud to authenticate wasn't that legit something Sony patented, like you have to stand up and go "I LOVE EATING AT ARBYS" to play your videogame or whatever?
|
|
|
|
Billiton sounds like the name of a snooty butler
|
|
|
|
Chris Knight posted:dev tittys
|
|
|
|
re: keyfob chat, i wear faggy gay girljeans sometimes that are so tight that removing my keys from my pocket is a legitimate challenge and my car not requiring me to do so is awesome. check your cargo pants privilege
|
|
|
|
Shaggar posted:just touch the door handle and it will automatically unlock if the fobs in ur pocket. yes that's the feature I'm saying is awesome. i thought the whole problem is that people could use POWER AMPLIFIERS (tm) to make it so you can touch the door while the keys are still in your house.
|
|
|
|
Bonfire Lit posted:I'd hope that the car would do challenge-response instead of just accepting any old replay, especially since it's the one initiating the conversation unlike the old push-button fobs from what I understand the car just has this counter in it and the keyfob has a counter and as long as the counters produce something within +- 200 counts of each other it's fine with it.
|
|
|
|
spankmeister posted:hai guise how do i intercepted ssl? nice av/post combo
|
|
|
|
Optimus_Rhyme posted:We guarantee our attribution is accurate as we paid for the more expensive MaxMinds GeoIP database i lol'd irl
|
|
|
|
Jabor posted:there was also one case where the mitm proxy wasn't actually validating certs itself, so when it was installed anyone could pull off a dumb-as-rocks self-signed mitm attack against you. but yeah, not using per-client keys is the most common fuckup. it was validating certs actually, but when a cert showed as invalid it would just rename the name to "<site>-invalid.com" or something like that. That's fine for the common name, but it completely ignored SAN's, so you could just make a SAN of "*.google.com" or whatever and it wouldn't touch it and your browser would just go "lol k looks legit to me"
|
|
|
|
|
|
|
|
Aleksei Vasiliev posted:Criminals won't pause before popping and unlocking. *groan*
|
|
|
|
it's been like 5+ years since that came out and every time it's posted i still have to watch the whole thing and giggle like an idiot the whole time.
|
|
|
|
https://developers.yubico.com/ykneo-openpgp/SecurityAdvisory%202015-04-14.htmlquote:The source code contains a logical flaw related to user PIN (aka PW1) verification that allows an attacker with local host privileges and/or physical proximity (NFC) to perform security operations without knowledge of the user’s PIN code. dammit yubikey you're the only hsm-y/smartcard thing I can afford do a better job 
|
|
|
|
Rufus Ping posted:openpgp card + usb smartcard reader is €35 http://shop.kernelconcepts.de/ doesn't seem to do NFC the way the yubikey does. they have ones with MiFARE but it just seems to be a separate chip stapled on. gotta have NFC for my poo poo phone for reasons.
|
|
|
|
Munkeymon posted:why'd they station it so low? less radiation hazard for the occupants? That (it's under the magnetic field and also beneath the Van Allen belts), plus less lifting like SIGSEGV said, plus if it's in the thin-but-still-there part of the atmosphere space junk only sticks around for like, a few months before re-entry compared to hundreds of thousands of years.
|
|
|
|
idk about that weird linux router thing but I heard that Netflix had some kind of breakthrough with their setup and that's why they're switching: http://arstechnica.com/security/2015/04/16/it-wasnt-easy-but-netflix-will-soon-use-https-to-secure-video-streams/ also I met Weev waaay back in like 2005 and can confirm he's a genuinely awful person.
|
|
|
|
Twenty-Seven posted:all messaging programs are the worst i unironically use Pidgin for everything (except IRC) because my friends are spread out across like 8 different protocols and gently caress if I'm gonna run the entire massive abortion that is the Steam client all the time just to chat to my bros. not IRC though cuz it sucks at IRC noticably more than it sucks in general, idk why
|
|
|
|
Snapchat A Titty posted:probably more likely than not We're the only species to figure out how to completely eliminate horrible diseases like smallpox, outright leave the planet and grace a literal other world thanks to our own ingenuity and determination, and also to decide that that poo poo was boring and expensive so let's just invest our money in murder robots and dragon dildos instead.
|
|
|
|
JumpinJackFlash posted:lol if you think that guy is going to jail. I mean he was already the super-rich son of an oligarch he probably stole this billion just for shits and giggles.
|
|
|
|
Daman posted:weev is managing to troll this thread without having an account. drat oh yeah like that rootkit where you'd freeze ram with freon and put it in another computer and root around in it looking for keys. root.
|
|
|
|

|
| # ¿ Apr 29, 2024 09:32 |
|
OSI bean dip posted:https://www.unitedstatescourts.org/federal/cand/284981/1-0.html Please accept a free year of Kroll identity monitoring at NO CHARGE!!!
|
|
|