|
Just set up a guest network at home on my Asus router, with the Asus Merlin firmware flashed to it. When I connect to the guest network I cannot see the samba share I have on my main network, as it should be. Are these guest networks on consumer routers pretty secure? Is it possible to 'see' from guest network to the other? How are they usually implemented? Using some kind of vlan?
|
|
|
|

|
| # ¿ Apr 27, 2024 06:24 |
|
Internet Explorer posted:They are usually another subnet with a firewall rule inbetween not to allow traffic. Thanks. I'm gonna leave it passwordless for a while to see how many connections it logs. Probably a bit risky for a residential area, but what the heck.
|
|
|
|
GobiasIndustries posted:This is really, really asking for trouble. unruly posted:Very much so. What goes out through your connection is your responsibility. Kiddy porn, harassment, etc. Noted and changed.
|
|
|
|
I listened to the latest episode of The Complete Privacy & Security podcast today and I'm very interested in dipping my toes into pfsense on my home network, running my current Asus RT-AC56U as merely a wireless access point and letting pfsense do the rest. The Protectli routers aren't available here in the UK but would possibly import one. Is there another box that would do a similar job? I really want pfsense but don't have the space in my server cabinet to do a 'build your own' version. Plus, it would be nice to just have a small, low power, box specifically designed for the job. edit: There are some on Amazon UK but I don't know which ones are reliable/good. They look similar to the Protectli ones though. apropos man fucked around with this message at 16:43 on Oct 16, 2017 |
|
|
|
Is there an idiots guide to setting up pfSense on a qotom mini PC? I've got just my laptop connected to port 2 on the miniPC and my modem connected to port 1 and I cannot get the web configurator page to load. I've messed about with it for 2 hours and need to sleep now. Will check this thread in the morning.
|
|
|
|
I've finally got pfSense up and running on my brand new Qotom Intel i3 MiniPC. Woohooo!! I have a TP-Link Archer set up as a dumb access point, connected to eth2 of the 4 LAN ports on the MiniPC and I have my cable modem plugged into eth1 and configured as WAN. So I have 2 spare ports: eth3 and eth4. I can access the pfSense configuration web GUI over WiFi from my laptop and I have internet through the WAN/modem. One question: I reckon I can get away with just using the other two spare ethernet ports on the back of the MiniPC: one for my home server and one going into a powerline connector in the wall outlet. pfSense names these extra ports as OPT1 and OPT2 by default if I want to use them. I realise that I can just rename them, but is it more appropriate to go out and buy a little 4 port switch, so that I have my entire LAN coming off one port? Or doesn't it matter?
|
|
|
|
bobfather posted:A switch for those extra devices will make it so they can still be seen and see each other if pfSense ever crashes or is down for maintenance. If you don't care about that feel free to plug them in to pfSense and give them access access to the rest of your network through your firewall rules. Cool. I think I'll use all native ports at the moment. I might actually want to stop/start the powerline independently of the network. If I expand into more devices later on I will buy a switch. Cheers.
|
|
|
|
Aaaargh. I've had such a lovely time getting my TP-Link C2 to act as an access point I'm thinking of getting just a dumb access point with no router. I went out this morning, after I'd posted on here and had everything working. Then I unplugged/replugged and booted everything and I cannot for the life of me get it working again. I think the firmware in the TP-Link is poo poo or something. The problem lies with the access point not getting DHCP from pfSense anymore. I've reverted back to my old setup, with the pfSense box unplugged and turned off. Is there a recommended access point for about £50 (UK) that will just plug into a pfSense box and only act as an access point with dual-band WiFi and a couple of LAN ports, not doing anything like DHCP or firewalling or anything? Just a switch with WiFi.
|
|
|
|
You know what, I think that's how I got it working in the first instance, before it went pear-shaped. It's too late to try now, but I'll have another crack at it in the morning. Cheers.
|
|
|
|
I came here to post a powerline question of my own: I've got a pair of ancient TP-Link AV500 adaptors and now they are starting to show their age by making the connection hang for about 10 seconds every few minutes. I guess they're about 5+ years old and overheating. I'm a bit better at configuring networking than I was 5 years ago and want to run the machine on a vlan. If I buy a pair of cheap TP-Link adaptors like these AV600's as a replacement will they handle a vlan tag on the packets?
|
|
|
|
If I'm connecting a pair of dumb powerline adaptors just to access 1 machine then it doesn't matter is the powerlines use vlan tagging or not, does it? So long as the switch that the pair of adaptors is connected to is tagging the packets and sending them via the vlan then the powerline doesn't have to get involved?? 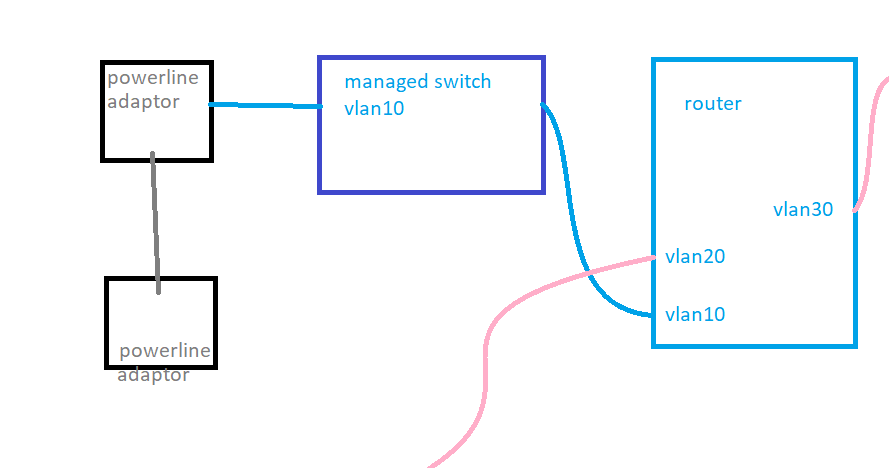
|
|
|
|
Is there any evidence to suggest that a WiFi AP 'wears out' quicker if you're using it at the edges of its radio distance? I installed a Ubiquiti AC Pro about a month ago and I'm very happy with it. If I buy another Pro to saturate my dwelling, apart from having the benefits of full AC everywhere, the load balancing will be pulling less juice on the current unit and therefore let the electronics run cooler, yes? This post sounds like I'm justifying spending more money, and I justly am! 🙂
|
|
|
|
Hmm. So tempted to buy another one. They're really nice units, and if I have two working together they'll last a good amount of time. Gonna do it 🙂😀
|
|
|
|
Unless I'm misunderstanding your last paragraph, you really want NAT turned back on.
|
|
|
|
Ashex posted:Pretty much this. Diagrams are fun so this is a lovely mockup of the setup: Oh, cool. I never thought about doing my own network diagram with one of those online tools. That should fill in the last half hour today :-D
|
|
|
|
ickna posted:... I'm doing just that, only using a Raspberry Pi instead of a full-size Linux box. From the Pi I can access other stuff. If you want to regularly transfer files and data over SSH then the RasPi will be lacking in throughput. It's good and discreet if you just want terminal access, though.
|
|
|
|
I recently got one of these to power my Ubiquiti AC Pro: https://www.amazon.co.uk/TRENDnet-E...ds=poe+injector I'm not really that aware of the differing standards but I believe that the AC Pro needs one of the higher rated injectors and this one is doing the job fine so far.
|
|
|
|
I've currently got a Raspberry Pi doing the Cloud Key job. It was as simple as starting with a fresh install of Raspbian, changing the host name to 'unifi' and following a guide to add the unifi repository then installing a few packages through apt: https://www.technologist.site/2016/06/02/how-to-install-ubiquiti-unifi-controller-5-on-the-raspberry-pi/3/ Works well if you have a RasPi lying round doing nothing.
|
|
|
|
I'm using a Pi3 too. I had a Pi2 plugged in via ethernet but I think I had trouble getting it to play nicely with my AC Pro's, since my ethernet is on a different subnet to my wireless. I switched to a Pi3 (which I also had lying around) and connected it via WiFi and once the Pi3 controller and my two AP's were all on the same subnet it worked right away. A Pi2 with a wireless USB adaptor plugged into it would give a similar effect.
|
|
|
|
I think I'm gonna add PiHole to my uniPi too, when I get round to it. I wasn't going to run it in a docker container, but that's an interesting proposition now you mention it. I think the Pi3 should be able to handle it. At the moment it's running just headless Raspbian with unifi, so it seems like a waste of clocks until I add PiHole too.
|
|
|
|
Does stubby integrate easily with PiHole? Last time I used PiHole was nearly a year ago. Interested in having encrypted DNS, too.
|
|
|
|
Well that sounds like a super little weekend project. Thanks man. EDIT: Although, it's probably gonna be a much slicker DNS experience if I use a second Pi that's plugged in via ethernet, rather than use the wireless Pi. I'm thinking WiFi latency might delay DNS too much if I point everything in my home network at it. Either a second Pi for PiHole/stubby or have another go at sorting the routing out between the UniPi and my AP's so that they can communicate with it from the AP subnet of 192.168.1.x when the Pi is on 192.168.0.x apropos man fucked around with this message at 22:28 on Jul 17, 2018 |
|
|
|
Noted. Thanks. EDIT: Further to my earlier post about getting the Pi controller working with my AP's whilst on a different subnet. I decided to disable WiFi on the Pi by nulling out wpa-supplicant, then physically plugging into a switch. When I rebooted I got the same deal I had a couple of months ago: an accessible UniFi controller interface that couldn't see my AP's. I gave the Pi controller a static IP and followed this guide: http://blog.gowifi.co.nz/2014/02/unifi-having-uaps-on-different-subnet.html SSH'ed into my AP's, one by one, and issued the set-inform command and gave them the new static address of my UniPi controller (that's now on a different subnet because it's cabled). code:apropos man fucked around with this message at 23:43 on Jul 17, 2018 |
|
|
|
Is it worth signing up for Gold? I've already got my pfSense box set up nicely and I manually make backups. I'm not an expert at configuring it but I can do what I need with it.
|
|
|
|
Bad PR for what? I know there was a fork but I'd already painstakingly set up pfSense, so I didn't bother investigating why someone had forked it.
|
|
|
|
Oh. Thanks. I guess it makes sense to keep an eye on Opnsense, then, and if the development there matches pfSense keeping the option open to swap over.
|
|
|
|
Does anyone use a standard desktop style fan inside their network cabinet? I'm using an Ikea cabinet, like this one:  Except mine has the wooden doors. In the left cupboard is a home server and in the right cupboard is:
The server obviously has its own fans to introduce a bit of airflow in the left cupboard. Is there a small desk fan or even something I could sticky tape to the wall of the networking side, just to introduce a bit of airflow? Emphasis would be on quietness. Things are getting a little hot in there but nothing seems like it's at the point of overheating.
|
|
|
|
Cheers. I don't have a spare Molex to power a PC fan (but I do have a selection of 80mm and 120mm fans that aren't in use). I was thinking about one of these: https://www.amazon.co.uk/gp/product/B00G059G86/ref=oh_aui_search_detailpage?ie=UTF8&psc=1 But the 120mm fans I have spare are a couple of nice Corsair ones and an NZXT one, so I think I'll go for a three-pack of these and see what the noise levels are like: https://www.amazon.co.uk/Male-Adapt...sb+to+fan+cable It's the cheapo option, so if that's too loud I can always go with the first one. It's a shame to have some nice case fans doing nothing.
|
|
|
|
Paul MaudDib posted:If you want to VLAN some stuff off, and your router doesn't support that, what's the cheapest way to get like a pfsense box set up? Ideally it would have a pretty low idle power, but I don't want it loving with gaming latency. Would something like the SG1000 be OK? Would there be any point in going to something like those PC-Engines boards? Depends on how much you regard as cheap, but my little qotom box has ran pfSense like a dream for the best part of a year. It's an i3, 4GB SODIMM and 32GB mSATA, so probably overkill for what you're looking for. I think the whole kaboodle was pushing $250 from AliExpress but it's gonna last me two or three years at least. Possibly more. The power drain is probably more than what you're looking for though. I say it runs like a dream, but I went out this morning and came back home and booted my laptop to find that my DHCP was non-existent. I went to my networking cabinet and loads of stuff was turned off: I found out after I booted everything up and checked my server logs that I'd had a brief power outage at around 10:30 am. Everything works again apart from the poo poo-cheap 8-port managed switch I was using to VLAN certain ports. I think the power outage has messed the config up. I was looking for a reason to swap it out with a much more expensive Ubiquiti US-8 port POE+ switch and it finally made me pull the trigger. At least the Ubiquiti unit will be a) more performant b) more reliable in an outage c) receive actual firmware updates and d) configurable on the same web interface I use for my Ubiquiti AP's. It's made me think about also getting a fairly low wattage UPS and bunging that in my networking cabinet, though. I don't mind too much about my other machines suddenly losing power but I'd like to have some level of protection on my networking equipment. Is there a recommended UPS that will supply about 4 UK plugs (pfSense mini-PC, Ubiquiti 150W across 8 ports switch (which I will never use to its full wattage), Raspberry Pi and modem)? Something around a hundred watts of protection would be fine. Do such things exist, rather than huge UPS boxes for servers? I just want something that provides continuity against short power outages of a couple of minutes and doesn't need to provide a heavy output. I live in a really built-up area so any outages are usually someone triggering a breaker in the next flat or whatever and the power is back on within a minute or two.
|
|
|
|
Would this be any good for providing 5 minutes of protection just for networking equipment: https://www.amazon.co.uk/APC-Back-U...+power+supplies As I said earlier, I'm not fussed about powering a BIG RIG with one, just 3 or 4 network devices.
|
|
|
|
Rexxed posted:It will provide up to 210 Watts for an unlisted amount of time. 5 minutes is probably doable. Bear in mind the model you linked has 3 battery backup IEC C13 outlets and one surge only. You'll need some of these if you want to plug transformers in: Yeah, I think I'll go with the low power one (in the old-skool beige colour) that I linked. It should be small enough to fit in my network cabinet and I can buy one of those adaptors to link it to a three way splitter, whilst my pfSense box will take a C13 connector straight into the brick. Cheers!
|
|
|
|
Question: If I buy this Ubiquiti US-8-150W switch:  Then what are the advantages of the two SFP sockets on the right hand side? If I buy another one further down the line, can I run fibre between two of these puppies and have one downstairs and one upstairs, effectively having a solid source of ethernet on both levels of a home? From what I've quickly read, the SFP sockets can accommodate CAT5/6 or fibre, depending on which adaptor you connect. Does one transmit and one receive if you connect them up to the same socket on the same type of unit, or are they both doing dual-direction of the traffic?
|
|
|
|
n0tqu1tesane posted:
Ah, so I guess you only need to connect a single SFP cable between boxes (fibre or RJ45) to get a decent connection? And I assume that doubling up with two lots of cables is for if you want an extreme/hardcore transfer rate? As for Pi-Hole, anyone trying it for the first time should be golden. It's so well scripted that it's a piece of cake to set up. I recently had mine running with encrypted DNS through cloudflare as per this guide: https://scotthelme.co.uk/securing-dns-across-all-of-my-devices-with-pihole-dns-over-https-1-1-1-1/ Someone linked to that guide on here and it worked well for a while. But then with the latest Pi-Hole update mine seemed to get broken. I think it's because Pi-Hole have stopped using dnsmasq and the guide I linked to uses dnsmasq. So I reverted back to using Pi-Hole normal unencrypted DNS.
|
|
|
|
CrazyLittle posted:(1) It's an 8-port PoE+ switch that has 48v 802.3af/at or 24v passive PoE on all 8 ports, (2)plus an additional two SFP sockets to plug in either copper 1000BASE-T SFP modules (and plug in cat5/cat6) or 1000BASE-SX / LH singlemode or multimode fiber patch cables. Since it's a (3)fully managed (lol enterprise) switch you can team multiple ports together with LACP and get (not really) double the bandwidth (4) with two ports teamed. That's handy for NAS servers or switch-to-switch uplinks. Chances are you're not going to stress even a single gigabit LAN, so those features are lost on 95% of users. You're a more knowledgeable at networking standards than I am, but I am looking to hook it up to a home system that's got decent throughput. I currently have: • 2x Unifi AC PRO (I plan to power one straight from the Unifi switch and the other is currently on a POE+ adaptor in the hallway), • miniPC router running pfSense (Haswell i3, 4GB RAM, mSATA SSD with 4 gigabit ports) • Raspberry Pi 3 running as the Unifi controller/web interface • Cheap and nasty TP-Link 8 port managed switch I'm running two WiFi VLANs on the AP's and also have 3 ports on the cheap switch tagged as separate VLANs: the rest are trunked. The cheap managed switch is a pain in the arse to configure VLAN's and involves removing it from the network completely and connecting directly to my laptop via cable and configuring a static IP just to get the web interface up. I didn't say I expected to get double the speed if I connected both SFP's with a second US-8-150W. As you say, there's also a 60W variant that doesn't have the SFP connectors and costs half the price. I reckon the cheaper one would be plenty to power one of my AC PRO's but I'm willing to pay the extra now, in case I want to conjoin two of them at a later date. I reckon I've spent somewhere in the region of £550 to have a nice home networking setup that should last a few years and I feel that the lovely £35 switch is letting the side down. It'll be really nice to be able to configure my VLANs in the same web interface as my AP's, too. Is there any reason why connecting two US-8-150W's with two cables wouldn't be beneficial in terms of latency? I'm thinking two pathways are better than one. If I'm ever in a situation where I'm gonna be making a hole somewhere to pass a cable through to an upstairs switch why not go the whole hog and pass two lines through? apropos man fucked around with this message at 23:38 on Aug 13, 2018 |
|
|
|
CrazyLittle posted:60W is enough for 4 PoE 802.3af 48v (15w max) ports. Which is also the number if PoE ports the US-8-60W has. I'm not sure what you mean by "conjoin two of them" means in the context of talking about APs. You'll likely never need to bond ports for an access point. Maybe conjoin was a stupid word to use (probably!). I meant join the two 150W switches and have an AP running from each: one upstairs and one downstairs. I know that I could get two of the cheaper ones and network them together with a length of CAT5 or CAT6 but, y'know, this is the Serious Hardware/Software Crap and I don't mind overdoing it just because it can be done. Aren't those SFP ports used exactly for this sort of purpose in data centers, where you'd have a bunch of regular ethernet ports on a rack server and then use SFP to bridge two servers together for a direct link? That's the way I'm imagining. EDIT: I think the penny has dropped as to what you're saying. There's not much point in buying the 150W over the 60W switch unless you're covering long distances with the SFP? Because you're still only getting a 1Gb throughput, which the 60W switch will also do? Is that what you're suggesting? apropos man fucked around with this message at 18:39 on Aug 14, 2018 |
|
|
|
Well I've realised that I almost wasted money on the 150W SFP version. I actually ordered one a couple of days ago but the Amazon seller cancelled my order the next day due to a mis-price (it was only underpriced by about £7). So I'm gonna get the 60W version of the same switch without the SFP. It'll still be interoperable with a second switch when I buy one, still do gigabit on the ports, still do VLANs via the Unifi web interface and still power up my AC-PRO's. So it does everything I want and I've saved myself £60 or £70! :-)
|
|
|
|
redeyes posted:^^^ For NIC drivers?! This makes me unhappy. A quick search suggests that it means that if you're actually using all ports at once then you'll get a full gigabit speed on each port. If you buy a cheap switch (like my TP-Link which is getting replaced when my Ubiquiti 8-port arrives this week) then you'll often find that the internals can't cope with delivering full gigabit on all ports at once: the bandwidth is shared internally. I guess it depends how cheaply made the switch is to how many ports at once you can get full gigabit on. There's probably a better, more in-depth explanation but you should be able to push all 16 ports with full duplex gigabit traffic all at once.
|
|
|
|
No shame in over-provisioning if you can afford it. I wish I'd never went the the cheap switch in the first place but I was a bit more naive about networking at the time. Still, it'll sit in a drawer for a few months and maybe get donated to someone eventually. Edit: I was replying to redeyes.
|
|
|
|
Is there no way that you can put a small Linux machine in between the second Xbox and your router, then map the port coming into the Linux box to an alternative port going out of it and then NAT the alternative port to go to the internet? I'm tired and really haven't thought this through properly, so it may be absolute codswallop advice.
|
|
|
|

|
| # ¿ Apr 27, 2024 06:24 |
|
Dr. Despair posted:Just finished setting a pi-hole up using a first gen RPI and I gotta say, this is pretty handy. Only problem setting it up was the fact that the raspian install I had sitting around was way too old to let me install it originally, but after doing a clean install it went together in just a few minutes. Yeah. They've done an awesome job on the install script. It's so slick. Have a go at running code:Has anyone got encrypted DNS working with the latest version? I had mine working with cloudflared but the latest update seems to have broken it, so I've reverted back to running it standard.
|
|
|




