|
ymgve posted:Someone claims to have broken the SIMON cipher on shorter keylenghts https://crypto.stackexchange.com/qu...sim/70471#70471 argues that the examples could have been found by brute force search without too much trouble
|
|
|
|

|
| # ¿ Apr 25, 2024 19:54 |
|
there's three listed authors though? 
|
|
|
|
no one has ever regretted treating network addresses as plain 32-bit ints
|
|
|
|
so i can monitor the location of any iphones within bluetooth radius?
|
|
|
|
i have a feeling a lot of rowhammer stuff is held because no one knows htf to fix it like we know it works in javascript and there are still barely any hardware or software mitigations so where are the drive by browser exploits
|
|
|
|
proposal: ecc ram with a small explosive charge that triggers after a set number of correctable errors the counter persists after restarts ofc
|
|
|
|
Harry Lime posted:This has been fun to follow this week looks more like mental illness than a scam to me  like you see this specific kind of kookery a lot and they always have some new mathematics or unbreakable crypto or what not
|
|
|
|
Lain Iwakura posted:hey. i am working on a semi-secret project and need some help. can y'all help me add to this list of RSS feeds that will provide me with infosec news? i specifically want infosec and even more so if they're often sensationalised. it helps if i do not need to add filters to parse out what is infosec and isn't https://www.theregister.co.uk/security/headlines.atom https://www.schneier.com/blog/atom.xml
|
|
|
|
Shaggar posted:thats not really the issue. the problem is changing the underlying behavior without changing the structure of the method leads to confusion amongst those who aren't really paying attention. Linux is right here when he says people should understand what they're doing and then ask specifically for the secure random if they need it. getrandom() was specifically added to have a correct way to request secure randomness /dev/random will start blocking very quickly as it uses a weird "depletable" model of entropy, which is bad /dev/urandom will mostly work like you want, but also it will just go ahead and return predictable data if you call it on boot before it has collected sufficient entropy, which is *catastrophic* the whole point of getrandom() is that it acts like urandom, *except* if you call it early on boot, where your program will actually block instead of, say, going ahead and generating RSA keys with factors common to other poor slobs who listened to the "just use urandom always" hacks and also it has a flag to act as urandom instead just for convenience.
|
|
|
|
python had to deal with this and tediously hashed out exactly what required blocking on entropy (anything that users in turn will be relying on to be secure) and what didn't (hash table randomization) https://bugs.python.org/issue26839 note that they spotted hangs of 90 seconds in the wild in all that time /dev/urandom on linux would have been happily pouring out faux randomness, which is why relying on secure numbers from /dev/urandom any time other people will be running your code in unpredictable circumstances is computer malpractice
|
|
|
|
the problem isn't drawing "too much randomness", the problem is that on linux reading urandom before it is well-seeded will not block, but instead give you nonrandom, predictable data we know this is a real world problem https://www.usenix.org/system/files/conference/usenixsecurity12/sec12-final228.pdf but somehow there's still a "just use urandom" meme going around and you get garbage articles like Cocoa Crispies posted:tom ptacek’s https://sockpuppet.org/blog/2014/02/25/safely-generate-random-numbers/ tpacek can bloviate as much as he wants but anyone can read the kernel source and verify that if your code relies on urandom being random it is catastrophically broken if someone calls it early enough after boot, where early enough can sometimes be within a minute if you make sure your code won't compile on linux or if you're only ever running it yourself and have hardware rng then sure but why risk it, just use getrandom(), unless linus fucks that up too
|
|
|
|
estimate one line of apl code per developer per week and hold daily scrums where everyone describes the current shape and contents of their array, and what array shape they hope to achieve by tomorrow
|
|
|
|
quote:Only sudoers entries where the ALL keyword is present in the Runas specifier are affected. i for one am removing all my untrusted users from wheel until this is fixed
|
|
|
|
Carbon dioxide posted:
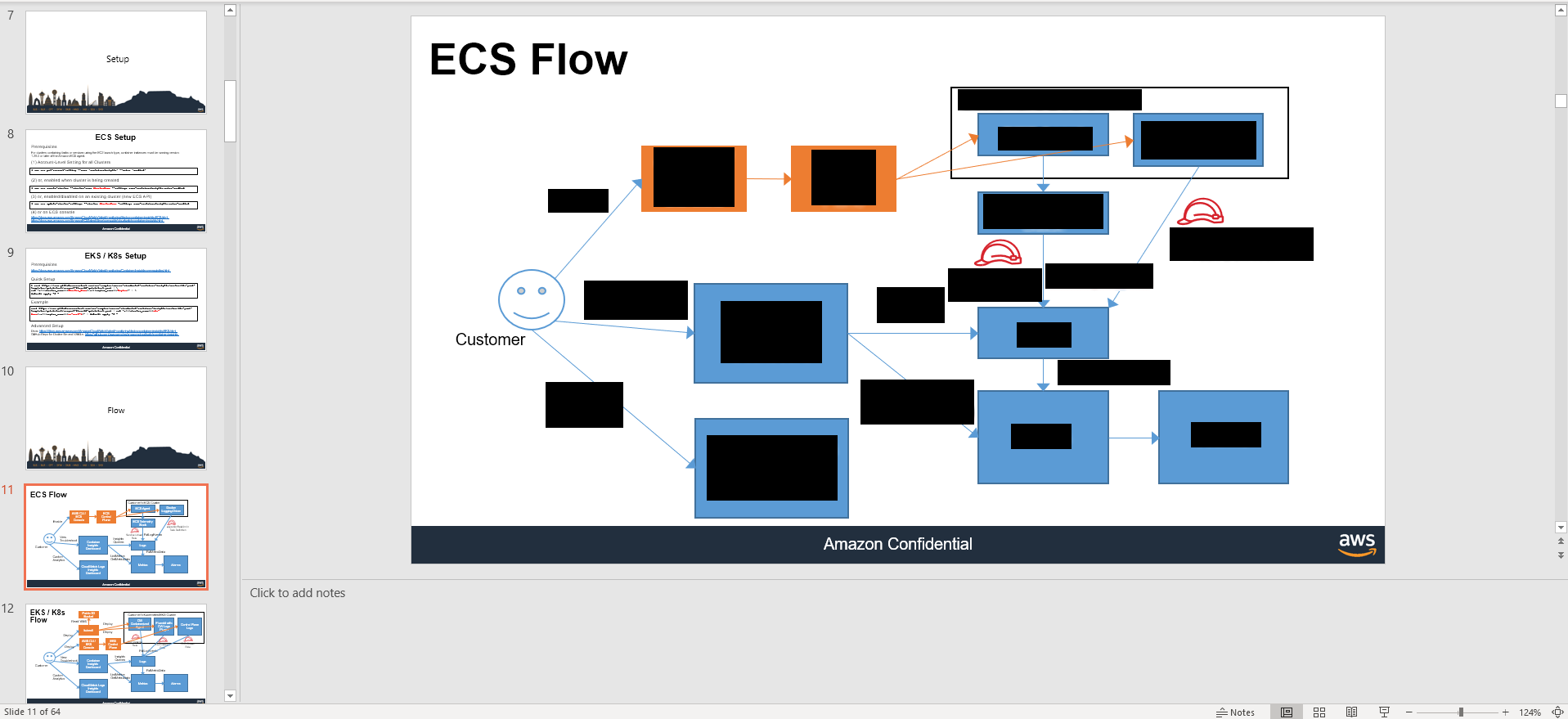
you could probably tell with a bit of squinting Container Insights Dashboard sends Insight Queries to ??? Custom Analytics goes to CloudWatch Logs Insights Dashboard
|
|
|
|
tbh i was confused because "turn off exposure notifications" sure is a wording that sounds like it would disable notifications but not the tracking product idea: a camera with a bluetooth receiver you put by the door and it tells you when any of your employees/customers mark themselves as having covid
|
|
|
|
you cant spell microchipping without chip + pin
|
|
|
|
is this where we talk about case sensitivityquote:When multiple dependencies differ only in the case of their name, Arborist's internal data structure saw them as separate items that could coexist within the same level in the node_modules hierarchy. However, on case-insensitive file systems (such as macOS and Windows), this is not the case. Combined with a symlink dependency such as file:/some/path, this allowed an attacker to create a situation in which arbitrary contents could be written to any location on the filesystem.
|
|
|
|
quiet day since half the company couldn't resolve slack.com due to their dnssecfuck https://lists.dns-oarc.net/pipermail/dns-operations/2021-September/021340.html seems to be over now but lol at your day if you're typing this https://status.slack.com/2021-09/06c1e17de93e7dc2 quote:In order to resolve this faster, your ISP (Internet Service Provider) will need to flush their DNS record for slack.com. Please reach out to your networking team to provide them with this information.
|
|
|
|

|
| # ¿ Apr 25, 2024 19:54 |
|
Potato Salad posted:pardon, what? hell yeah big fan of performance art
|
|
|