|
Captain Foo posted:it appears you have committed to not issuing a new thread title, but then a new thread title was issued what went well: • prior thread title will be not be revoked due to secfuck concerns of our goonposters
|
|
|
|

|
| # ? Jun 3, 2024 15:38 |
|
Captain Foo posted:it appears you have committed to not issuing a new thread title, but then a new thread title was issued we are recommending to all of our subscribers that they not change titles, but some of them are in very important threads Prevent 2024-05-21
|
|
|
|
Subjunctive posted:we are recommending to all of our subscribers that they not change titles, but some of them are in very important threads Hahahhaha
|
|
|
|
Thank you for your comments and questions. Your entrussy will be addressed in our June 7 report to Mozilla.
|
|
|
|
c secfuck s: at the office we've collectively gone down a rabbit hole that started with "hey, why is there an internet-equipped air conditioner somewhere trying to resolve weird DNS queries" and is now onto "why is this internet-equipped air conditioner running SSLv3 and nothing newer"
|
|
|
|
charitable answer: scada?
|
|
|
|
Kazinsal posted:c secfuck s: at the office we've collectively gone down a rabbit hole that started with "hey, why is there an internet-equipped air conditioner somewhere trying to resolve weird DNS queries" and is now onto "why is this internet-equipped air conditioner running SSLv3 and nothing newer" I feel like a better question should be "why is there an internet equipped air conditioner on the general network instead of vlan'd into its own little corner?"
|
|
|
|
when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind
|
|
|
|
Kazinsal posted:c secfuck s: at the office we've collectively gone down a rabbit hole that started with "hey, why is there an internet-equipped air conditioner somewhere trying to resolve weird DNS queries" and is now onto "why is this internet-equipped air conditioner running SSLv3 and nothing newer" SSLv3 is probably the least of your worries here
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind 
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind lol
|
|
|
|
Captain Foo posted:it appears you have committed to not issuing a new thread title, but then a new thread title was issued Subjunctive posted:we are recommending to all of our subscribers that they not change titles, but some of them are in very important threads Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind
|
|
|
|
Captain Foo posted:it appears you have committed to not issuing a new thread title, but then a new thread title was issued it was clearly stated that IF a new thread title would be re-issued, the content of the thread would remain the same. we'll provide another update on the thread by 6-28-2024
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind lol
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind 
|
|
|
|
Beve Stuscemi posted:Lmao high security cooling fan
|
|
|
|
I gotta buy Ben an account.
|
|
|
|
https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c21 Our new friend gives an update (and doesn't answer Wayne's leading questions but cest la vie): quote:Here is our progress: good news: they do provide a spreadsheet of subscriber breakdown of delayed certs bad news: of the 8 thousand pending certs, there's only six reasons given in total and the breakdown looks like this  eta: there's 7 here due to pivot table weirdness, but it's definitely 6 Raymond T. Racing fucked around with this message at 05:03 on May 22, 2024 |
|
|
|
Raymond T. Racing posted:https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c21 ... So what do they do when it's the regular cert expiration time? Are all teams choreographed months in advance so that they can all turn the key simultaneously?
|
|
|
|
Raymond T. Racing posted:https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c21 quote:Revoking the affected certificates within the prescribed deadline may cause significant harm; the certificates are used in critical infrastructure and cannot be safely replaced prior to the revocation deadline. The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows. I'm on a razor's edge of doxxing myself and posting for the first time to this incident report. What a loving joke. Hey assholes, if this was as a result of key compromise your self made up "extensions" and "exceptions" are a joke. As a CA you literally cannot grant extensions, exceptions or exclusions from BR agreed policies. As a CA by virtue of being allowed the privilege of issuing certificates on behalf of the Internet you're beholden to aforementioned policies. That they posted redacted customer names when they're all publicly available via CT logs is laughable. Volmarias posted:... So what do they do when it's the regular cert expiration time? Are all teams choreographed months in advance so that they can all turn the key simultaneously? Most companies roll their certs when they receive an alert from their NOC or monitoring systems telling them a cert is expiring within 48 hours. 72 if they're functionally competent and doing it manually. 60+ days is a joke and only because Entrust basically said "don't worry about rushing this because WE won't revoke your certs because you're paying us and we understand that your company doesn't want to do this under duress. The emails that Entrust sent out to their customers/subscribers basically said, "we may have done an oopsie, WE however do not believe it was that big of an oopsie, and we're going to give you as much time as we can possibly stall for, because we fundamentally don't believe WE were in the wrong, some mean people on the Internet with our entire business model in the balance however do, and we have a proven track record of being able to deflect these issues and issue statements stating we will not screw up this way in the future, and they've believed us in the past, as such we're going to give you as much time as you find convenient to do what we've asked (replace these certs) and keep the charade going for us." What Entrust should have been [morally, and contractually] obligated to say is: "It has come to our attention through a third party that we mis-issued certificates, which your account was part of, and under the CA/B agreed upon guidance of 4.20.69 (insert more here) this/these certificates <serials> will be revoked in 5 business days under CA/B agreed upon guideline(s) <relevant parts> please reissue your affected certificates <list> via our portal or contact our customer support at 1-888-867-5309 for further information" SeaborneClink fucked around with this message at 06:13 on May 22, 2024 |
|
|
|
Volmarias posted:... So what do they do when it's the regular cert expiration time? Are all teams choreographed months in advance so that they can all turn the key simultaneously? they set a calendar reminder 3 months in advance to start looking for a new job so that it's someone else's problem
|
|
|
|
Raymond T. Racing posted:https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c21 lmao all of those are the same reason just with slightly different/reordered words
|
|
|
|
SeaborneClink posted:Hey assholes, if this was as a result of key compromise your self made up "extensions" and "exceptions" are a joke. sure they can it's right there and by doing so they get a competitive advantage through creating less hassle for their customers than the other CAs would race to the bottom baby
|
|
|
|
Raymond T. Racing posted:when people said entrust's institutional failures would have a chilling effect on the ecosystem i definitely didn't have this outcome in mind hehehe
|
|
|
|
as mentioned itt entrust did provide a vague breakdown on cpsuri, but i've fixed their terrible reasons and gave a breakdown per-subscriber: https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c24 also i made a post on m-d-s-p that's been in my back of my mind for a bit: https://groups.google.com/u/1/a/mozilla.org/g/dev-security-policy/c/OKzHYta8AxM
|
|
|
|
Telia posted their analysis, in which I could find no mention of their internal subscribers refusing to cooperate. And no action items about not letting internal company politics override their responsibility as a CA… edited to add a link https://bugzilla.mozilla.org/show_bug.cgi?id=1896108
|
|
|
|
zokie posted:Telia posted their analysis, in which I could find no mention of their internal subscribers refusing to cooperate. And no action items about not letting internal company politics override their responsibility as a CA…
|
|
|
|
Curious if anyone plans to ask Telia "If a similar incident happens in 1 month, where an error in the certificate is considered unimportant to the customer, will they also be allowed to delay revocation in violation of policy? If so, why even have the policy, since apparently it is optional? If not, can you confirm that you would in fact revoke the certificate even if the subscriber is responsible for critical infrastructure?"
|
|
|
|
https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c25quote:(In reply to Wayne from comment #18) finally replies to Wayne's old post and ignores the actual breakdown with feedback
|
|
|
|
Raymond T. Racing posted:https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c25 lol they didn't actually give all the details. basically none of the dates requested were provided and the reasons are such horseshit: 44 of them have the base reason and nothing else "Revoking the affected certificates within the prescribed deadline may cause significant harm; the certificates are used in critical infrastructure and cannot be safely replaced prior to the revocation deadline." 16 have this reason in addition to base reason: "Subscriber advises that it uses a manual process of installation for replacing the affected certificates, which takes more time. The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows." 2218 have the base reason plus this: "The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows." 5928 with base reason plus this: "The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows. Subscriber advises that it uses a manual process of installation for replacing the affected certificates, which takes more time." 7 with this: "The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows. The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows." 367 with the base and this: "The Subscriber needs additional time to coordinate replacement with multiple teams, external companies and with change management process/windows. The Subscriber needs additional time to coordinate replacement with multiple teams."
|
|
|
|
I’d also be curious to see if they actually got positive confirmation from these subscribers or they’re just assuming that if the customer hasn’t responded or created a new cert it’s too difficult to do it in the timespan required
|
|
|
|
The more important the application the more important it is that your cert is right and that you can fix issues quickly.
|
|
|
|
Raymond T. Racing posted:I’d also be curious to see if they actually got positive confirmation from these subscribers or they’re just assuming that if the customer hasn’t responded or created a new cert it’s too difficult to do it in the timespan required
|
|
|
|
https://inti.io/p/when-privacy-expires-how-i-got-accessquote:As part of a large-scale privacy investigation, I have bought more than 100 [expired] domain names previously belonging to social welfare and justice institutions in Belgium. What I observed was unsettling. Scary stuff.
|
|
|
|
low temps, high security!
|
|
|
|
yeah sadly not too surprising. there should be proper disposal procedures for all of these and data sent encrypted with a key by different means but lol at the firms involved getting the resources to do that
|
|
|
|
Raymond T. Racing posted:https://bugzilla.mozilla.org/show_bug.cgi?id=1886532#c25 I love how they're just painting themselves into a corner more and more. "Won't revoke, not a big deal, they're real busy and can't do it now." That got a lot of push back and pointed comments towards 'you are required to do this, you clowns'. Now they've pivoted to "Can't revoke, critical infrastructure, will cause actual harm." And Wayne, long may he reign as king of secfuck finding, kneecaps it immediately by pointing out the massive carve-out they gave themselves preventing the super important customers from using those certs for anything a sane person would call 'critical'. Apparently an internal decision of 'our customers would lose money, blame us, and therefore cost us money, it is critical we don't piss them off' somehow managed to transmute itself to using 'critical infrastructure' as a reason publicly.
|
|
|
|
seems bad: https://env.fail/posts/firewreck-1/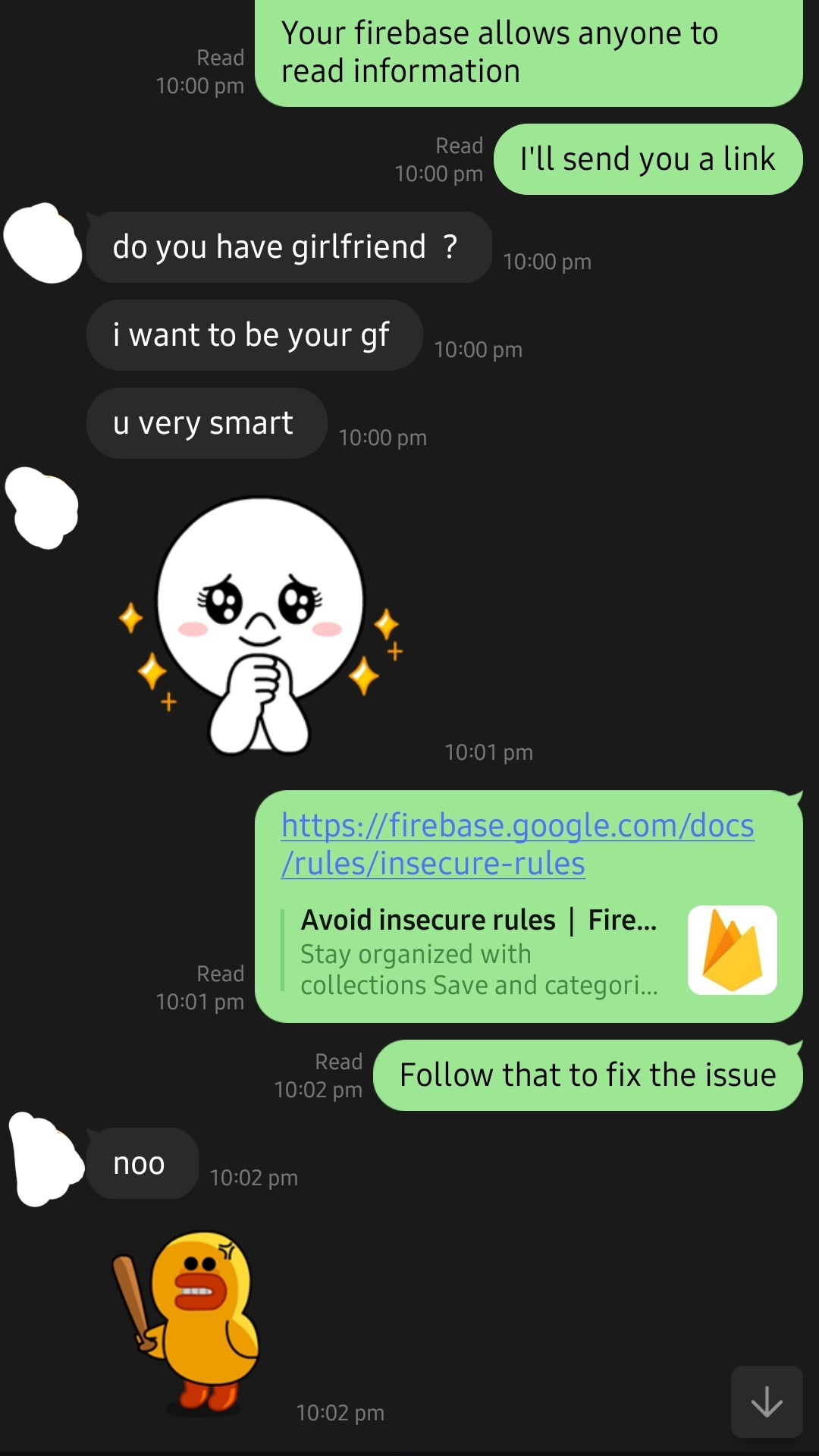 https://x.com/xyz3va/status/1793307173822378258
|
|
|
|

|
| # ? Jun 3, 2024 15:38 |
|
Methylethylaldehyde posted:I love how they're just painting themselves into a corner more and more. I think you will find that the infrastructure is Very Critical while also not being on that list. Was it this gently caress that was almost totally certs at some bank, or another? Because I suspect they could figure out how to rotate those certs if they were told they actually need to.
|
|
|