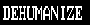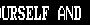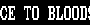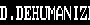|
perfect
|
|
|
|

|
| # ? Apr 26, 2024 20:38 |
|
 is it possible that this is an exploit payload and that's how it looks on non-vulnerable phones?
|
|
|
|
Alien invasion was supposed to be September, they're jumping around with the script too much 
|
|
|
|
ymgve posted:
anything is possible, but i'd say its more likely something got hosed up by the spit and twine that underlies wireless messaging that or someone pasted something in from word.
|
|
|
|
ymgve posted:
look who forgot they subscribed to Zalgo alerts
|
|
|
|
ymgve posted:
I saw an explanation on twitter that the GSM encoding could literally miss a bit and turn "t " into "h<control code>" and hey presto buffer overflow but I don't know how accurate that is. GSM uses absolutely garbage CRCs so it checks out in my mind
|
|
|
|
https://twitter.com/cdespinosa/status/1268760428903104518?s=19
|
|
|
|
already gone
|
|
|
|
ymgve posted:
Looks like a bit flip, or a malformed continuation header. I tried to decode it; I ended up going down a rabbit hole. Did you know that between SMS and MMS there was EMS? and that it had it's own vector graphics format. Wireless Vector Graphics. I have yet to find a reference to anyone actually implementing it anywhere. but it's still floating around, and the last change to the spec was in 2016 (although the byzantine labirynth that is the 3gpp specs may have me a tad confused.) I am now determined(-ish) to track down a phone capable of sending/receiving EMS message with a wireless vector graphic in it.
|
|
|
|
Midjack posted:already gone 
|
|
|
|
Yeah this probably disappeared as it looks to be a false ID
|
|
|
|
ya it looks like it was a false positive. however it still stands that the real security gently caress up is posting your location data in to a publicly viewable website
|
|
|
|
Kuvo posted:ya it looks like it was a false positive. however it still stands that the real security gently caress up is posting your location data in to a publicly viewable website Isn't that literally the purpose of social media and other tracking apps?
|
|
|
|
No, the purpose of social media and other tracking apps is to build an advertising profile for targeted mind control. Encouraging you to make your private information public so it can be slurped into the advertising database is one strategy to accomplish this goal.
|
|
|
|
pseudorandom name posted:No, the purpose of social media and other tracking apps is to build an advertising profile for targeted mind control. itís generally in the interests of those doing the collection to have exclusive access to the corpus, though, and not to have it generally available
|
|
|
|
We determined this wasn't him
|
|
|
|
"Good workout, really nice weather. Had to stop to beat up a kid but I still got a PR on the segment!"
|
|
|
|
fins posted:Did you know that between SMS and MMS there was EMS? and that it had it's own vector graphics format. Wireless Vector Graphics. I have yet to find a reference to anyone actually implementing it anywhere. but it's still floating around, and the last change to the spec was in 2016 (although the byzantine labirynth that is the 3gpp specs may have me a tad confused.) I am now determined(-ish) to track down a phone capable of sending/receiving EMS message with a wireless vector graphic in it. EMS was definitely implemented. No idea about WVG. Another ex-Motorolan pointed me towards T720 which is a 2002 featurephone that according to gsmarena has "EMS 5.0".
|
|
|
|
Used to work with a Bell Labs guy who worked on the signaling for ISDN and some of the stuff it used was really cool, makes me want to gently caress around with some of that equipment. No SecFucks here, but it would be fun to deep dive.
|
|
|
|
taqueso posted:"Good workout, really nice weather. Had to stop to beat up a kid but I still got a PR on the segment!" I was confused by this post because I use PB for personal best and PR for git Pull Request. Edit: Oh wait I actually have secfuck news. The Dutch national health organisation has this internet form they ask volunteers to fill in. They don't ask your name but they do want your postal code, birth year and e-mail address. And since Dutch postal codes only are like 20 houses by codes, that's probably enough to identify people exactly if they want to. They also ask a whole bunch of medical questions, whether you have any Corona symptoms and so on. They use this as one of the many data sources to see how the disease is spreading. Anyway, that's been open since the start of the epidemic here in March, and now it turns out that if you just increment the ID number in the form's URL one by one you get to see what other people filled in including the aforementioned personal information. The journalist built a quick script as a PoC and got 50 people's form responses in a minute or two. At the very least, the journalist told the organisation first who took the form offline, and also apparently the form results were moved from the web server to another system nightly, so you couldn't use this to get data more than 24 hrs old. Carbon dioxide fucked around with this message at 07:44 on Jun 7, 2020 |
|
|
|
Are WeChat passwords all handled in plaintext?stephenthinkpad posted:LOL We're kind of in a cold war so it might be a made up story, but it seems easy enough to independently try it out yourself
|
|
|
|
Dumb Lowtax posted:Are WeChat passwords all handled in plaintext? sure, you just need a friend who already uses wechat hope they donít get banned too
|
|
|
|
WeChat passwords could be handled completely competently, just that changing the password gives you the opportunity to detect badwords.txt
|
|
|
|
The twitter thread links to a reddit thread where 1. someone claims to have tried the same but they weren't banned and 2. someone suspects that the Chinese firewall just has the keys to wechat's SSL certificates so they can MiTM the change request and then it's them who ask Wechat to ban the user.
|
|
|
|
~Coxy posted:WeChat passwords could be handled completely competently, just that changing the password gives you the opportunity to detect badwords.txt yup, it's not even that uncommon to run them against a list of known bad/compromised passwords and then slap the user with a "no, stupid, don't use passw0rd! as your password"
|
|
|
|
Dumb Lowtax posted:Are WeChat passwords all handled in plaintext? It is entirely possible that the password being requested also goes to another service on the backend as part of its journey for censor checking without needing to be stored permanently; the censor just has to press the "OK/NOT OK" button and not ok calls the state's WeChat API for permabanning someone.
|
|
|
|
https://www.youtube.com/watch?v=1hs451PfFzQ using Bayesian analysis on the Zelda Windwaker RNG to write tools to help speedrunners get through the battleship minigame.
|
|
|
|
I was setting up a new machine and came up with a dumb question. Generally itís acceptable to have one private ssh key per client for all services. This, after all, is just a private key to identify myself as a client so it makes sense to just be the same key everywhere. But I like the idea of generating separate keys for separate services, but it seems kind of unnecessary when I think about it. As long as Iím generating a key from >512 bits and everything then I donít really have to worry about using a single key. What is this thread's opinion on that?
|
|
|
|
There are reasons not to use the same key everywhere beyond limiting scope if a key is compromised, including but not limited to: https://rushter.com/blog/public-ssh-keys/ Anyway, OpenSSH is deprecating RSA keys in a future release.
|
|
|
|
PCjr sidecar posted:There are reasons not to use the same key everywhere beyond limiting scope if a key is compromised, including but not limited to: https://rushter.com/blog/public-ssh-keys/ Thanks for the warning. Also this amused me: https://blog.filippo.io/ssh-whoami-filippo-io/ Someone apparently downloaded all of the public keys from Github.
|
|
|
|
PCjr sidecar posted:There are reasons not to use the same key everywhere beyond limiting scope if a key is compromised, including but not limited to: https://rushter.com/blog/public-ssh-keys/ Anyone happen to know if there are options for using other key types on a Yubikey 5?
|
|
|
|
https://twitter.com/GossiTheDog/status/1270019914720514048
|
|
|
|
Cool cool https://twitter.com/__agwa/status/1270054737317113857
|
|
|
|
stallmand again
|
|
|
|
CmdrRiker posted:As long as Iím generating a key from >512 bits if you're using rsa this isn't nearly long enough. anyone can factor it for a few dollars for comparison, CAB baseline requirements require 2048 bit rsa
|
|
|
|
cybrancyborg posted:Anyone happen to know if there are options for using other key types on a Yubikey 5? when i got a new yubikey for my usb-c laptop (p sure that's a yubikey 5 model) i generated ed25519 keys on it and it's fine with that 
|
|
|
|
CmdrRiker posted:As long as Iím generating a key from >512 bits since it came up anyway; you should also possibly have some of the bits be non-zero. though i guess imposing that restriction removes some randomness.
|
|
|
|
because of some complicated rotation thing they were trying to do, which apparently didnít actually rotate anything anyway
|
|
|
|
ROT-26 cipher duh
|
|
|
|

|
| # ? Apr 26, 2024 20:38 |
|
Subjunctive posted:because of some complicated rotation thing they were trying to do, which apparently didnít actually rotate anything anyway It sounds like once it rotated it was OK but before then it was using 0 Session resumption is such a footgun, though gnutls really went out of their way to make it especially footguny with the custom TOTP thing
|
|
|